Types of Phishing Attacks and How to Prevent Them
Interested in security? Follow along for content within Cybersecurity
Social engineering is a manipulation technique that tricks users into making security mistakes or providing sensitive information. Phishing is a form of social engineering and is one of the popular social engineering attacks. In this article, we’ll explain what phishing is and go over 3 of the most common types of phishing attacks. With each type, we’ll explain best practices on how to protect yourself against them.

What is Phishing?
Phishing attacks are one of the most common attacks used by attackers to obtain sensitive information such as user credentials and credit card information. Attackers typically gain access to such sensitive information via email, social media, phone calls or any other form of communication where they can steal valuable data. It is a broad term used to gather sensitive information from people, but there are many types of phishing attacks.




Implementing a security awareness program to educate the employees about the different types of phishing attacks is a must. However, there are different ways to avoid each type of phishing attack as described below.





How to Recognize Phishing Attacks: Simple Methods
Spelling and grammar mistakes: You can easily recognize if you have received a phishing email if there are any spelling and grammar mistakes. Reputable companies don’t make mistakes in their emails.

Email body requests personal information




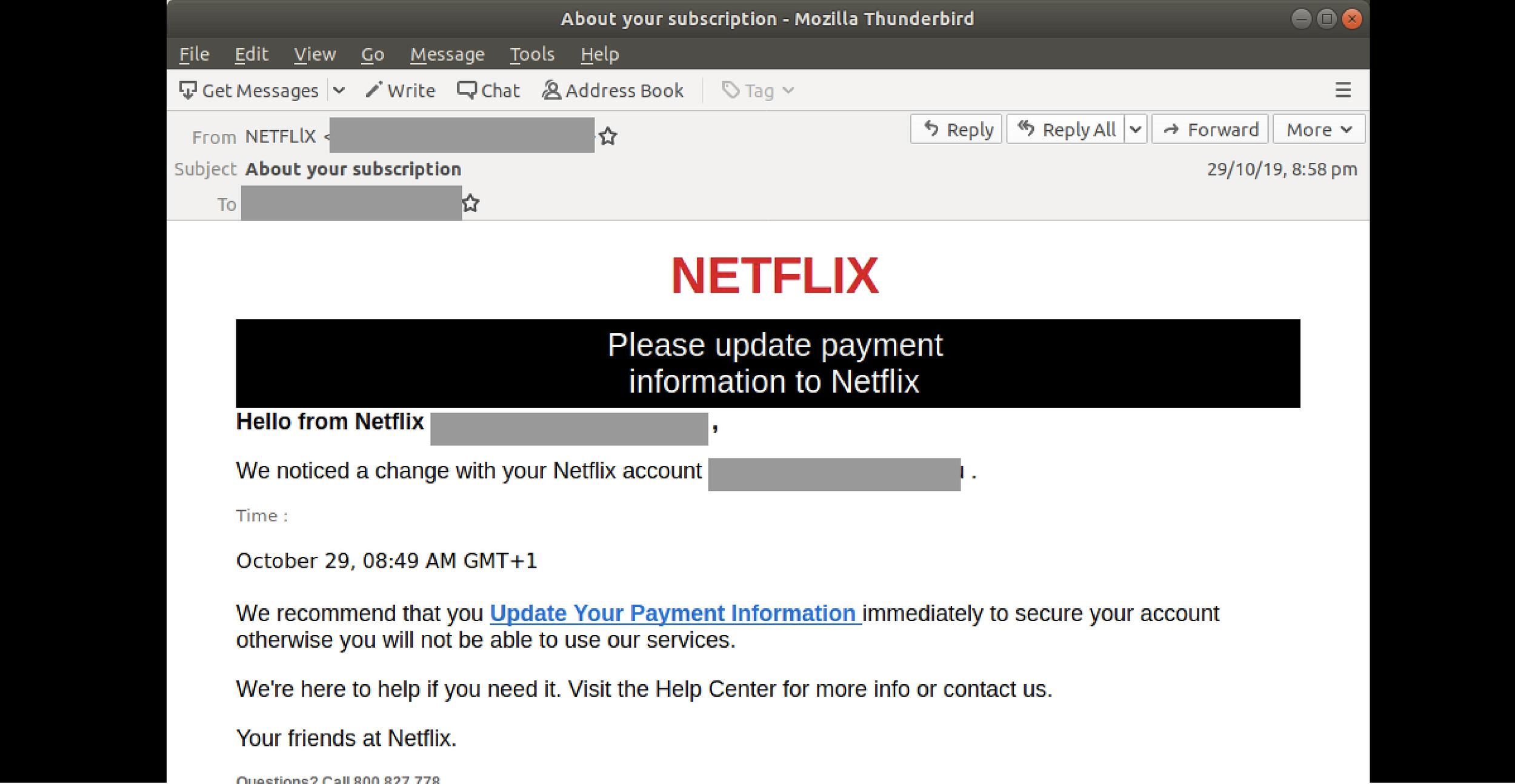
If you receive an email from a company asking you to provide personal information such as bank account number or your login credentials. Take this Netflix phishing email from 2019 below as an example. It was sent to users with the display name 'NETFLIX' or 'Netflix-Online'. Users were asked to update their payment information and for those who actually clicked on the link, would be brought to a page that looks like a Netflix branded login page. Once the users have submitted in their credit card information, the hackers now have access to all of this information. All the hackers had to do was make the fake phishing page look real by replicating Netflix's logo and their payment page.




Mismatched URL




If you hover over a URL link without clicking on it you can see the full address and if the URL does not match the hovered link then it could be a fake address




Unexpected email




Receiving an email stating that you won a competition that you never entered or asking you to click on a link to claim your prize. If it sounds too good to be true, it always is. Trust me, you don’t have a long lost ancestor in Turkey looking to give you your $10,000,000 inheritance over email.



Common Types of Phishing Attacks and Techniques
1. Spear Phishing




Spear phishing is delivered via email and targeted towards a specific organization, individual or business. The body of the email may contain a link or an attachment to download. The attacker’s objective is to get users to give up a little bit of information about themselves (i.e. personally identifiable data). Spear phishing attacks work because the emails look legit and believable to the end user. Attackers usually focus on a specific individual to eventually gain critical data such as bank accounts, work credentials, login credentials, and more. The attacker may not also be interested in a particular individual, but use this individual as a foot into an organization’s confidential data.



How to Prevent Spear Phishing Attacks




Security teams should train all employees on how to recognize and report suspicious emails. They should make sure that they have the necessary technology and processes to prevent, detect and respond to these types of threats. Security teams should strive to stay ahead of attackers by researching and learning about updated threat intelligence. It is important to note that it is not possible to discover a new spear phishing attack by analyzing it in isolation.

2. Whaling




Whaling attacks target senior management of an organization; typically these attacks consist of an attacker sending an email to upper management stating that the company is getting sued and they need to click on a URL link to receive more information. The only reason why whaling attacks are effective is due to human error.




How to Prevent Whaling Attacks




Use two-factor authentication for email accounts




Perform mock whaling attacks on employees to demonstrate how easy it is to be tricked




Establish some sort of a verification process such as face-to-face or verification over the phone for bank related questions




Educating employees and implementing appropriate security measures will help decrease the chance of a whaling attack to occur




3. Vishing




Vishing is a type of phishing attack that uses the phone system or VOIP. A common Vishing attack is an automated call to a user stating that there is an issue with their credit card account. The user is encouraged to validate their credit card information (credit card number, expiration date, and card security code). The objective of Vishing is to steal a person’s identity or money.




How to Prevent Vishing Attacks




Do not pick up the phone especially if you do not recognize the caller ID




Hang up the phone as soon as you suspect the phone call is suspicious




Do not respond to text messages where they ask you to press buttons or respond to prompts




Verify the caller’s identity by searching for the phone number on Google to identify if it is a spam number




Phishing attacks are still popular today and according to Symantec, one in every 2,000 emails are phishing emails which means that there are roughly 135 million phishing attacks every day (MetaCompliance). Phishing attacks are not going anywhere anytime soon and still occur frequently as we saw with the Netflix phishing email example.




Based on my professional and personal experience, till this day, I still see people falling for phishing attacks and provided attackers information without realizing it. Therefore, it is important that organizations educate and train their employees to understand what phishing attacks are and how to recognize them. This type of an attack must be consistently reminded of and discussed on a periodic basis.
This article was first published here: https://hackernoon.com/3-types-of-phishing-attacks-and-how-to-prevent-them-lh16345m

Comments
Post a Comment